Table of Contents (click to expand)
A dirtbox is a device that can intercept your calls and messages by masquerading as a cell phone tower. A similar device with more advanced features is the StingRay tracker. There are countermeasures to dirtboxes, such as cryptophones, that have a built-in firewall to identify and thwart requests from dirtboxes.
What if I told you that the phone calls you make and the messages you send to your best friend via a mobile network can be intercepted and listened to by others? It sounds a little creepy or paranoid, but it’s actually a possibility. A dirtbox is such a device that can conduct this dirty job of eavesdropping on cellular conversations.
Recommended Video for you:
Dirtbox, Aka DRT Box
To better understand how your mobile phone catches a signal, click here, and to learn about the detailed working of a mobile cell tower, click here.
The United States Marshals Service is presently using dirtboxes mounted on aircraft to detect and locate cell phones, especially those they deem suspicious. Dirtbox also collects information and records communications that happen through cell phones. Moreover, they can also be used to jam mobile phone communication.
Why Is It Called A Dirtbox?
You may wonder why this technology has been given such a grimy name. Well, the name stems from the company that originally developed it – Digital Receiver Technology. It is known by the abbreviation DRT in technical circles.
According to Digital Receiver Technology’s documentation, DRT is capable of cracking the encryption on communications from over 200 mobile phones at the same time. This is done across state-of-the-art 4G LTE frequencies used for fast voice and data communication. In 2008, Boeing took over the Digital Receiver Technology company. Boeing describes this device’s purpose as “jamming, managed access and detection”.
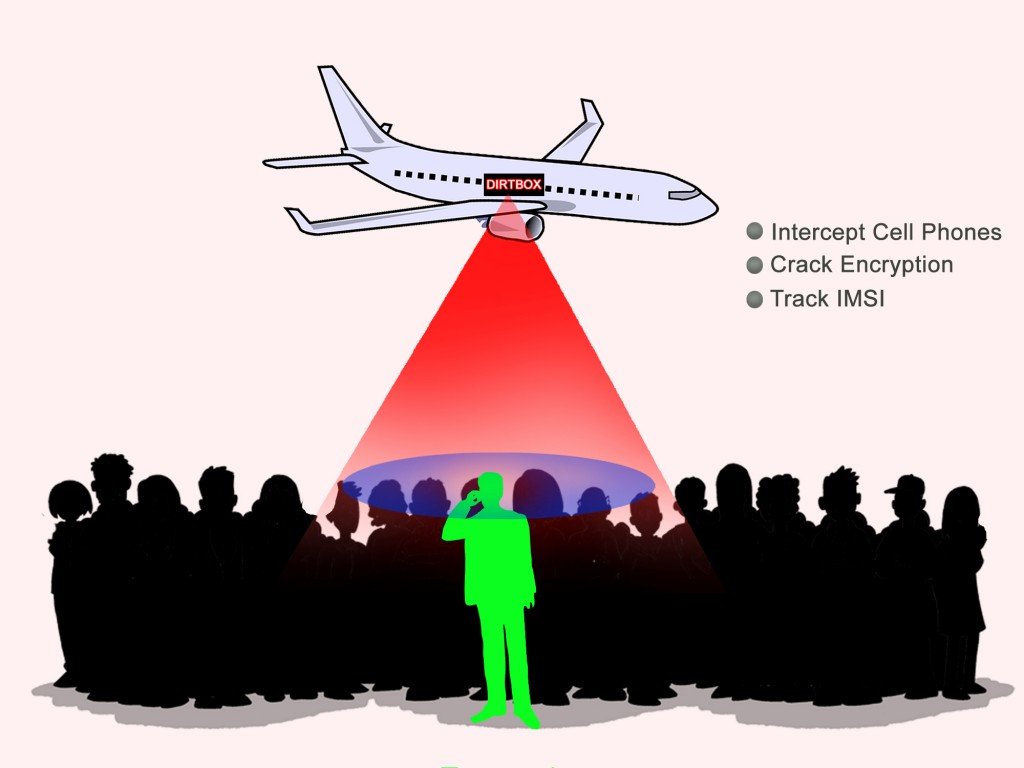
What Does The Dirtbox Do?
Dirtboxes basically operate as fake mobile phone towers, forcing all the (targeted) mobile phones within its range to use their signal for communication purposes. In other words, a dirtbox functions as a cell tower simulator. Also, as the information passes through the cell tower simulator, the dirtbox simultaneously breaks the encryption on the voice and data transmissions of dozens of mobile phones. If you put dirtboxes on an airplane or even a drone, you’ll potentially elicit all sorts of information about hundreds of people. This information shockingly includes recorded telephone conversations, identification of callers and receivers, and even SMSes shared between them.

What’s more frustrating is that cell phones automatically connect to these fake cell towers without the owner of the cell phone even knowing, because cell phones are designed to seek out the strongest signal in a given area. This implies that even if there are working towers in a given area, a dirtbox will theoretically boost its power and make itself more attractive for cell phones in the vicinity to connect to it. Thus, the cellphones are duped into choosing a dirtbox over a legitimate cell tower, which is how the game of monitoring and tracking begins.
A similar device with more advanced features is being used by US federal agencies, including the FBI, and is known by the name StingRay tracker.
What Is StingRay?
The StingRay is an advanced version of a dirtbox. Technically, it an IMSI-catcher with both active (cell site simulation) and passive (signal analysis) capabilities. Every SIM that you use in a mobile device has an international mobile subscriber identity (IMSI) number that is unique and usually consists of fifteen digits. An IMSI number is a must for every SIM operating on a Global System for Mobile Communications (GSM) or a Universal Mobile Telecommunications System (UMTS) network.
Caption: StingRay device by Harris Corp.

Origin And Purpose Of StingRay
The Florida-based Harris Corporation is the primary manufacturer of StingRay devices. In 2010, they started vehement negotiations with the Federal Communications Commission (FCC) to license their StingRay technology for use by state and local law enforcement. This was part of their business strategy to expand their market beyond the U.S. military and federal agencies. The license mandated that the FBI would manage any local acquisition of StingRay devices by domestic authorities. To keep its grip over this stealth technology tight, the FBI decreed that any state/local authority needs to sign a nondisclosure agreement before it is granted access to the StingRay device. Presently, StingRay devices are being used domestically in around 23 states, along with the District of Columbia, where it is used by the National Security Agency.
In the past, the tracking of cellular phones by police was done in conjunction with wireless operators. To track a cellular device, police needed a warrant specifying trap and trace orders. With this warrant in place, police could force any wireless operator to turn over their data to empower the law enforcement department to track specific mobile phones.
However, with the advent of dirtboxes like StingRay, police and other government organizations can enact their surveillance measures with ease. Just like a more advanced dirtbox, StingRay is designed to duplicate cell sites, mimic cell signals to break into cellular phones of the targeted individual(s), intercept their data, and track the phone’s location, even when it’s dormant! Also, the best part of this surveillance method for police is that it eliminates the need for coming up with a conditional warrant.

It’s a no-brainer to understand why police agencies are hesitant to discuss the use of the StingRay publicly. Even the manufacturers of the device are tight-lipped over the detailed working mechanism of this device.
Although StingRays are the most popular cell phone surveillance devices on the private market, other devices are used for the same purpose, including TriggerFish, Gossamer, Amberjack, Hailstorm, Harpoon and Kingfish.
Is There A Way Out?
After reading about the function and purpose of dirtboxes, you may wonder whether there is a way to get away from the prying eyes of such a surveillance device.
A number of countermeasures to dirtboxes have been developed to bypass monitoring. Cryptophones have been borne out of that purpose. Cryptophones have a built-in firewall to identify and thwart requests from dirtboxes like StingRay. They even alert the user whenever a cell tower requests an IMEI capture. In this way, the user has more control over what types of transmission take place between his cell phone and the cell tower.